| Voir le sujet précédent :: Voir le sujet suivant |
| Auteur |
Message |
joem
Modérateur

Inscrit le: 28 Jan 2006
Messages: 295
Localisation: a coté de trignac
|
 Posté le: 02 Avr 2012 à 23:45 Sujet du message: Virus sirefef.BV.2 [ RESOLU ] Posté le: 02 Avr 2012 à 23:45 Sujet du message: Virus sirefef.BV.2 [ RESOLU ] |
 |
|
Bonsoir,
Suite à un virus problème de connexion, bug...etc...
Voici le résultat du rapport ZHPDiag
http://cjoint.com/?BDcxFsaYlty
Merci
_________________

Dernière édition par joem le 02 Mai 2012 à 0:16; édité 1 fois |
|
| Revenir en haut de page |
|
 |
zaede
Equipe de sécurité
Inscrit le: 07 Déc 2007
Messages: 593
Localisation: est
|
 Posté le: 03 Avr 2012 à 16:39 Sujet du message: Posté le: 03 Avr 2012 à 16:39 Sujet du message: |
 |
|
Bonjour loem, salement enrhumé cette machine. On va la soigner
Attention le temps de téléchargement du script a été limité à 4 jours
- Clique sur http://cjoint.com/?3DdqLQQWg8u
- Sur la page qui s'ouvre clic droit et Tout sélectionner
- Refais un clic droit et Copier
- Double clique sur ZHPFix qui est sur le bureau.
** Pour Vista et Seven fais un clic droit sur le fichier téléchargé et Exécuter en tant qu'administrateur
- Clique maintenant sur le H bleu  (coller les lignes helper) (coller les lignes helper)
- Le texte copié dans le presse papiers s'affichera dans la fenêtre de ZHPFix
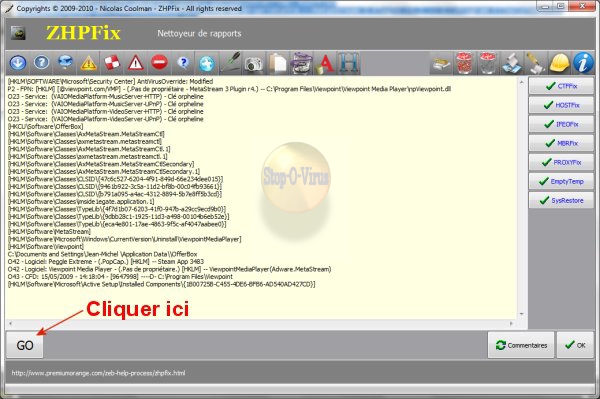
- Clique sur Go patiente le temps du traitement
- Un rapport nommé ZHPFixReport.txt sera créé et sauvegardé sur le bureau poste son contenu dans ta prochaine réponse
Le rapport se trouve également dans c:\ZHP
** Redémarre ton PC et poste le rapport de ZHPFix
====================================================
Le rapport posté, passe à ceci:
- Télécharge Roguekiller (par tigzy) sur le bureau
http://www.sur-la-toile.com/RogueKiller/
- Quitte tous tes programmes en cours
- Lance RogueKiller.exe.
- Sous Vista/Seven, clique droit et lancer en tant qu'administrateur
- Attendre que le Prescan ait fini ...
- Clique sur Scan.
Clique sur Rapport et copier coller le contenu du notepad dans la prochaine réponse |
|
| Revenir en haut de page |
|
 |
joem
Modérateur

Inscrit le: 28 Jan 2006
Messages: 295
Localisation: a coté de trignac
|
 Posté le: 03 Avr 2012 à 22:35 Sujet du message: Posté le: 03 Avr 2012 à 22:35 Sujet du message: |
 |
|
Bonsoir Zaede,
Merci de ton aide. Ce n'est plus un rhume ! c'est une bronchiolite infectieuse. 
Voici 1er rapport ( ZHPFix report )
Rapport de ZHPFix 1.12.3381 par Nicolas Coolman, Update du 08/02/2011
Fichier d'export Registre :
Run by Joem at 03/04/2012 22:03:42
Windows XP Professional Service Pack 3 (Build 2600)
Web site : http://www.premiumorange.com/zeb-help-process/zhpfix.html
Web site : http://nicolascoolman.skyrock.com/
========== Clé(s) du Registre ==========
SUPPRIME Key: HKCU\Software\Grand Virtual
SUPPRIME Key: CLSID BHO: {3806b089-6759-411d-b2c3-b7995a9f34d7}
SUPPRIME Key: HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{00000000-6E41-4FD3-8538-502F5495E5FC}
SUPPRIME Key: HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{D4027C7F-154A-4066-A1AD-4243D8127440}
SUPPRIME Key: HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Settings\{D4027C7F-154A-4066-A1AD-4243D8127440}
ABSENT Key: HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\MenuOrder\Start Menu2\Programs\Toolbar
ABSENT Key: CLSID BHO: {3806b089-6759-411d-b2c3-b7995a9f34d7}
========== Valeur(s) du Registre ==========
SUPPRIME [HKCU\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser]:{D4027C7F-154A-4066-A1AD-4243D8127440}
========== Dossier(s) ==========
SUPPRIME Folder: C:\Program Files\Everest Poker.net
SUPPRIME Folder: C:\Program Files\Conduit
SUPPRIME Folder: C:\Documents and Settings\Joem\Local Settings\Application Data\Conduit
SUPPRIME Temporaires Windows: : 177
SUPPRIME Flash Cookies: 8
========== Fichier(s) ==========
SUPPRIME File: c:\windows\tasks\at1.job
SUPPRIME File: c:\windows\tasks\at10.job
SUPPRIME File: c:\windows\tasks\at11.job
SUPPRIME File: c:\windows\tasks\at12.job
SUPPRIME File: c:\windows\tasks\at13.job
SUPPRIME File: c:\windows\tasks\at14.job
SUPPRIME File: c:\windows\tasks\at15.job
SUPPRIME File: c:\windows\tasks\at16.job
SUPPRIME File: c:\windows\tasks\at17.job
SUPPRIME File: c:\windows\tasks\at18.job
SUPPRIME File: c:\windows\tasks\at19.job
SUPPRIME File: c:\windows\tasks\at2.job
SUPPRIME File: c:\windows\tasks\at20.job
SUPPRIME File: c:\windows\tasks\at21.job
SUPPRIME File: c:\windows\tasks\at22.job
SUPPRIME File: c:\windows\tasks\at23.job
SUPPRIME File: c:\windows\tasks\at24.job
SUPPRIME File: c:\windows\tasks\at25.job
SUPPRIME File: c:\windows\tasks\at26.job
SUPPRIME File: c:\windows\tasks\at27.job
SUPPRIME File: c:\windows\tasks\at28.job
SUPPRIME File: c:\windows\tasks\at29.job
SUPPRIME File: c:\windows\tasks\at3.job
SUPPRIME File: c:\windows\tasks\at30.job
SUPPRIME File: c:\windows\tasks\at31.job
SUPPRIME File: c:\windows\tasks\at32.job
SUPPRIME File: c:\windows\tasks\at33.job
SUPPRIME File: c:\windows\tasks\at34.job
SUPPRIME File: c:\windows\tasks\at35.job
SUPPRIME File: c:\windows\tasks\at36.job
SUPPRIME File: c:\windows\tasks\at37.job
SUPPRIME File: c:\windows\tasks\at38.job
SUPPRIME File: c:\windows\tasks\at39.job
SUPPRIME File: c:\windows\tasks\at4.job
SUPPRIME File: c:\windows\tasks\at40.job
SUPPRIME File: c:\windows\tasks\at41.job
SUPPRIME File: c:\windows\tasks\at42.job
SUPPRIME File: c:\windows\tasks\at43.job
SUPPRIME File: c:\windows\tasks\at44.job
SUPPRIME File: c:\windows\tasks\at45.job
SUPPRIME File: c:\windows\tasks\at46.job
SUPPRIME File: c:\windows\tasks\at47.job
SUPPRIME File: c:\windows\tasks\at48.job
SUPPRIME File: c:\windows\tasks\at5.job
SUPPRIME File: c:\windows\tasks\at6.job
SUPPRIME File: c:\windows\tasks\at7.job
SUPPRIME File: c:\windows\tasks\at8.job
SUPPRIME File: c:\windows\tasks\at9.job
ABSENT Folder/File: c:\program files\conduit
ABSENT Folder/File: c:\documents and settings\joem\local settings\application data\conduit
SUPPRIME Temporaires Windows: : 3235
SUPPRIME Flash Cookies: 3
========== Tache planifiée ==========
SUPPRIME Task: At1
SUPPRIME Task: At11
SUPPRIME Task: At13
SUPPRIME Task: At15
SUPPRIME Task: At17
SUPPRIME Task: At19
SUPPRIME Task: At21
SUPPRIME Task: At23
SUPPRIME Task: At25
SUPPRIME Task: At27
SUPPRIME Task: At29
SUPPRIME Task: At3
SUPPRIME Task: At31
SUPPRIME Task: At33
SUPPRIME Task: At35
SUPPRIME Task: At37
SUPPRIME Task: At39
SUPPRIME Task: At41
SUPPRIME Task: At43
SUPPRIME Task: At45
SUPPRIME Task: At47
SUPPRIME Task: At5
SUPPRIME Task: At7
SUPPRIME Task: At9
========== Récapitulatif ==========
7 : Clé(s) du Registre
1 : Valeur(s) du Registre
5 : Dossier(s)
52 : Fichier(s)
24 : Tache planifiée
End of clean in 03mn 53s
========== Chemin de fichier rapport ==========
C:\ZHP\ZHPFix[R1].txt - 03/04/2012 22:03:42 [4424]
___________________________________________________
___________________________________________________
___________________________________________________
2ème rapport ( rogueKiller )
RogueKiller V7.3.2 [20/03/2012] par Tigzy
mail: tigzyRK<at>gmail<dot>com
Remontees: http://www.sur-la-toile.com/discussion-193725-1-BRogueKillerD-Remontees.html
Blog: http://tigzyrk.blogspot.com
Systeme d'exploitation: Windows XP (5.1.2600 Service Pack 3) 32 bits version
Demarrage : Mode normal
Utilisateur: Joem [Droits d'admin]
Mode: Recherche -- Date: 03/04/2012 22:21:00
¤¤¤ Processus malicieux: 0 ¤¤¤
¤¤¤ Entrees de registre: 99 ¤¤¤
[SUSP PATH] HKUS\.DEFAULT[...]\Windows : load (C:\WINDOWS\TEMP\128215ED48E067B912A3.exe,) -> FOUND
[SUSP PATH] HKUS\S-1-5-18[...]\Windows : load (C:\WINDOWS\TEMP\128215ED48E067B912A3.exe,) -> FOUND
[SUSP PATH] At16.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At15.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At14.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At13.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At12.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At11.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At10.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At1.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At25.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At24.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At23.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At22.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At21.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At20.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At2.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At19.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At18.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At17.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At34.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At33.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At32.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At31.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At30.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At3.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At29.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At28.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At27.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At26.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At43.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At42.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At41.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At40.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At4.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At39.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At38.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At37.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At36.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At35.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At52.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At51.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At50.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At5.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At49.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At48.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At47.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At46.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At45.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At44.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At61.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At60.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At6.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At59.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At58.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At57.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At56.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At55.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At54.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At53.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At70.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At7.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At69.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At68.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At67.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At66.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At65.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At64.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At63.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At62.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At8.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At79.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At78.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At77.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At76.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At75.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At74.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At73.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At72.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At71.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[SUSP PATH] At89.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At88.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At87.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At86.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At85.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At84.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At83.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At82.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At81.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At80.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At96.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At95.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At94.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At93.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At92.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At91.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At90.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> FOUND
[SUSP PATH] At9.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> FOUND
[HJ] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> FOUND
¤¤¤ Fichiers / Dossiers particuliers: ¤¤¤
¤¤¤ Driver: [CHARGE] ¤¤¤
SSDT[25] : NtClose @ 0x80567AED -> HOOKED (Unknown @ 0xF8B21DD4)
SSDT[41] : NtCreateKey @ 0x8057376F -> HOOKED (Unknown @ 0xF8B21D8E)
SSDT[50] : NtCreateSection @ 0x80565333 -> HOOKED (Unknown @ 0xF8B21DDE)
SSDT[53] : NtCreateThread @ 0x80578803 -> HOOKED (Unknown @ 0xF8B21D84)
SSDT[63] : NtDeleteKey @ 0x80597FFA -> HOOKED (Unknown @ 0xF8B21D93)
SSDT[65] : NtDeleteValueKey @ 0x80595C1A -> HOOKED (Unknown @ 0xF8B21D9D)
SSDT[68] : NtDuplicateObject @ 0x805748C2 -> HOOKED (Unknown @ 0xF8B21DCF)
SSDT[98] : NtLoadKey @ 0x805AF5C3 -> HOOKED (Unknown @ 0xF8B21DA2)
SSDT[122] : NtOpenProcess @ 0x80574AA9 -> HOOKED (Unknown @ 0xF8B21D70)
SSDT[128] : NtOpenThread @ 0x8059323B -> HOOKED (Unknown @ 0xF8B21D75)
SSDT[177] : NtQueryValueKey @ 0x8056A419 -> HOOKED (Unknown @ 0xF8B21DF7)
SSDT[193] : NtReplaceKey @ 0x8064FE82 -> HOOKED (Unknown @ 0xF8B21DAC)
SSDT[200] : NtRequestWaitReplyPort @ 0x8056DC86 -> HOOKED (Unknown @ 0xF8B21DE8)
SSDT[204] : NtRestoreKey @ 0x8064FA19 -> HOOKED (Unknown @ 0xF8B21DA7)
SSDT[213] : NtSetContextThread @ 0x8062E33F -> HOOKED (Unknown @ 0xF8B21DE3)
SSDT[237] : NtSetSecurityObject @ 0x8059D2BD -> HOOKED (Unknown @ 0xF8B21DED)
SSDT[247] : NtSetValueKey @ 0x8057BC5B -> HOOKED (Unknown @ 0xF8B21D98)
SSDT[255] : NtSystemDebugControl @ 0x8064AA57 -> HOOKED (Unknown @ 0xF8B21DF2)
SSDT[257] : NtTerminateProcess @ 0x805839B9 -> HOOKED (Unknown @ 0xF8B21D7F)
S_SSDT[549] : Unknown -> HOOKED (Unknown @ 0xF8B21E06)
S_SSDT[552] : Unknown -> HOOKED (Unknown @ 0xF8B21E0B)
IRP[IRP_MJ_INTERNAL_DEVICE_CONTROL] : atapi.sys -> HOOKED ([MAJOR] prosync1.sys @ 0xF8A3F6C1)
¤¤¤ Infection : ZeroAccess ¤¤¤
[ZeroAccess] (LOCKED) windir\NtUpdateKBxxxx present!
¤¤¤ Fichier HOSTS: ¤¤¤
127.0.0.1 localhost
¤¤¤ MBR Verif: ¤¤¤
+++++ PhysicalDrive0: WDC WD1600AAJB-22WRA0 +++++
--- User ---
[MBR] 9b8fe57175eadd014c86f40063d33463
[BSP] 70dd8b4b891dfafb3a751a70cfbce75c : Windows XP MBR Code
Partition table:
0 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 63 | Size: 49999 Mo
1 - [XXXXXX] EXTEN-LBA (0x0f) [VISIBLE] Offset (sectors): 102398310 | Size: 102618 Mo
User = LL1 ... OK!
User = LL2 ... OK!
Termine : << RKreport[1].txt >>
RKreport[1].txt
_________________
 |
|
| Revenir en haut de page |
|
 |
zaede
Equipe de sécurité
Inscrit le: 07 Déc 2007
Messages: 593
Localisation: est
|
 Posté le: 04 Avr 2012 à 16:46 Sujet du message: Posté le: 04 Avr 2012 à 16:46 Sujet du message: |
 |
|
Bonjour joem, oui en effet
Étape 1
Relance Roguekiller et clique sur Suppression
Poste le rapport ensuite
Étape 2
Télécharge AdwCleaner ( d'Xplode )
Enregistre ce fichier sur le bureau et pas ailleurs
- Double clique sur AdwCleaner.exe qui est sur le bureau.
** Pour Vista et Seven fais un clic droit sur le fichier téléchargé et Exécuter en tant qu'administrateur
- Clique sur Suppression laisse l'outil travailler
- Le scan terminé, le bloc notes s'ouvrira avec le résultat du scan. Poste son contenu dans ta prochaine réponse.
Note : Le rapport est également sauvegardé sous C:\AdwCleaner[S1].txt
Étape 3
Télécharge AntiZeroAcces
Lance le:
Répond Yes (oui) à la question, en tapant sur Y puis Entrée
Si le fix trouve l’infection, des lignes rouges doivent apparaître.
Le fix informe qu’un des fichiers systèmes a été patché et propose de le nettoyer.
Tape Y (oui) et Entrée pour lancer le nettoyage.
Si l’opération a réussi, tu verras le message Cleaned en vert.
Appuie sur une touche et redémarre l’ordinateur. |
|
| Revenir en haut de page |
|
 |
joem
Modérateur

Inscrit le: 28 Jan 2006
Messages: 295
Localisation: a coté de trignac
|
 Posté le: 04 Avr 2012 à 22:36 Sujet du message: Posté le: 04 Avr 2012 à 22:36 Sujet du message: |
 |
|
Bonsoir zaede, voici les rapports.
Étape 1
RogueKiller V7.3.2 [20/03/2012] par Tigzy
mail: tigzyRK<at>gmail<dot>com
Remontees: http://www.sur-la-toile.com/discussion-193725-1-BRogueKillerD-Remontees.html
Blog: http://tigzyrk.blogspot.com
Systeme d'exploitation: Windows XP (5.1.2600 Service Pack 3) 32 bits version
Demarrage : Mode normal
Utilisateur: Joem [Droits d'admin]
Mode: Suppression -- Date: 04/04/2012 22:04:49
¤¤¤ Processus malicieux: 2 ¤¤¤
[SUSP PATH] 6d4mFfF7.exe -- C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> KILLED [TermProc]
[SUSP PATH] 6d4mFfF7.exe -- C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> KILLED [TermProc]
¤¤¤ Entrees de registre: 98 ¤¤¤
[SUSP PATH] HKUS\.DEFAULT[...]\Windows : load (C:\WINDOWS\TEMP\128215ED48E067B912A3.exe,) -> DELETED
[SUSP PATH] At16.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At15.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At14.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At13.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At12.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At11.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At10.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At1.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At25.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At24.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At23.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At22.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At21.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At20.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At2.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At19.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At18.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At17.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At34.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At33.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At32.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At31.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At30.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At3.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At29.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At28.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At27.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At26.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At43.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At42.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At41.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At40.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At4.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At39.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At38.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At37.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At36.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At35.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At52.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At51.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At50.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At5.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At49.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At48.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At47.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At46.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At45.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At44.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At61.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At60.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At6.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At59.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At58.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At57.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At56.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At55.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At54.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At53.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At70.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At7.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At69.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At68.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At67.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At66.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At65.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At64.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At63.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At62.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At8.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At79.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At78.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At77.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At76.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At75.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At74.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At73.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At72.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At71.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[SUSP PATH] At89.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At88.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At87.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At86.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At85.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At84.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At83.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At82.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At81.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At80.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At96.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At95.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At94.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At93.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At92.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At91.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At90.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe_ -> DELETED
[SUSP PATH] At9.job @ : C:\Documents and Settings\All Users\Application Data\6d4mFfF7.exe -> DELETED
[HJ] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> REPLACED (0)
¤¤¤ Fichiers / Dossiers particuliers: ¤¤¤
¤¤¤ Driver: [CHARGE] ¤¤¤
SSDT[25] : NtClose @ 0x80567AED -> HOOKED (Unknown @ 0xF8B9E9C4)
SSDT[41] : NtCreateKey @ 0x8057376F -> HOOKED (Unknown @ 0xF8B9E97E)
SSDT[50] : NtCreateSection @ 0x80565333 -> HOOKED (Unknown @ 0xF8B9E9CE)
SSDT[53] : NtCreateThread @ 0x80578803 -> HOOKED (Unknown @ 0xF8B9E974)
SSDT[63] : NtDeleteKey @ 0x80597FFA -> HOOKED (Unknown @ 0xF8B9E983)
SSDT[65] : NtDeleteValueKey @ 0x80595C1A -> HOOKED (Unknown @ 0xF8B9E98D)
SSDT[68] : NtDuplicateObject @ 0x805748C2 -> HOOKED (Unknown @ 0xF8B9E9BF)
SSDT[98] : NtLoadKey @ 0x805AF5C3 -> HOOKED (Unknown @ 0xF8B9E992)
SSDT[122] : NtOpenProcess @ 0x80574AA9 -> HOOKED (Unknown @ 0xF8B9E960)
SSDT[128] : NtOpenThread @ 0x8059323B -> HOOKED (Unknown @ 0xF8B9E965)
SSDT[177] : NtQueryValueKey @ 0x8056A419 -> HOOKED (Unknown @ 0xF8B9E9E7)
SSDT[193] : NtReplaceKey @ 0x8064FE82 -> HOOKED (Unknown @ 0xF8B9E99C)
SSDT[200] : NtRequestWaitReplyPort @ 0x8056DC86 -> HOOKED (Unknown @ 0xF8B9E9D8)
SSDT[204] : NtRestoreKey @ 0x8064FA19 -> HOOKED (Unknown @ 0xF8B9E997)
SSDT[213] : NtSetContextThread @ 0x8062E33F -> HOOKED (Unknown @ 0xF8B9E9D3)
SSDT[237] : NtSetSecurityObject @ 0x8059D2BD -> HOOKED (Unknown @ 0xF8B9E9DD)
SSDT[247] : NtSetValueKey @ 0x8057BC5B -> HOOKED (Unknown @ 0xF8B9E988)
SSDT[255] : NtSystemDebugControl @ 0x8064AA57 -> HOOKED (Unknown @ 0xF8B9E9E2)
SSDT[257] : NtTerminateProcess @ 0x805839B9 -> HOOKED (Unknown @ 0xF8B9E96F)
S_SSDT[549] : Unknown -> HOOKED (Unknown @ 0xF8B9E9F6)
S_SSDT[552] : Unknown -> HOOKED (Unknown @ 0xF8B9E9FB)
IRP[IRP_MJ_INTERNAL_DEVICE_CONTROL] : atapi.sys -> HOOKED ([MAJOR] prosync1.sys @ 0xF8A3F6C1)
¤¤¤ Infection : ZeroAccess ¤¤¤
[ZeroAccess] (LOCKED) windir\NtUpdateKBxxxx present!
¤¤¤ Fichier HOSTS: ¤¤¤
127.0.0.1 localhost
¤¤¤ MBR Verif: ¤¤¤
+++++ PhysicalDrive0: WDC WD1600AAJB-22WRA0 +++++
--- User ---
[MBR] 9b8fe57175eadd014c86f40063d33463
[BSP] 70dd8b4b891dfafb3a751a70cfbce75c : Windows XP MBR Code
Partition table:
0 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 63 | Size: 49999 Mo
1 - [XXXXXX] EXTEN-LBA (0x0f) [VISIBLE] Offset (sectors): 102398310 | Size: 102618 Mo
User = LL1 ... OK!
User = LL2 ... OK!
Termine : << RKreport[3].txt >>
RKreport[1].txt ; RKreport[2].txt ; RKreport[3].txt
----------------------------------------------------------------------------------------------------------
Étape 2
# AdwCleaner v1.504 - Rapport créé le 04/04/2012 à 22:17:09
# Mis à jour le 01/04/2012 par Xplode
# Système d'exploitation : Microsoft Windows XP Service Pack 3 (32 bits)
# Nom d'utilisateur : Joem - JOEM-PC
# Exécuté depuis : E:\Documents\Téléchargements\adwcleaner.exe
# Option [Suppression]
***** [Services] *****
***** [Fichiers / Dossiers] *****
***** [H. Navipromo] *****
***** [Registre] *****
[*] Clé Supprimée : HKLM\SOFTWARE\Classes\Toolbar.CT1264369
Clé Supprimée : HKCU\Toolbar
Clé Supprimée : HKCU\Software\Conduit
Clé Supprimée : HKLM\SOFTWARE\Conduit
Clé Supprimée : HKLM\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\0563B8630D62D75ABBC8AB1E4BDFB5A899B24D43
***** [Navigateurs] *****
-\\ Internet Explorer v8.0.6001.18702
[OK] Le registre ne contient aucune entrée illégitime.
-\\ Mozilla Firefox v11.0 (fr)
Nom du profil : default
Fichier : C:\Documents and Settings\Joem\Application Data\Mozilla\FireFox\Profiles\fmwyab9z.default\prefs.js
[OK] Le fichier ne contient aucune entrée illégitime.
*************************
AdwCleaner[S1].txt - [302 octets] - [04/04/2012 22:13:45]
AdwCleaner[S2].txt - [1167 octets] - [04/04/2012 22:17:09]
########## EOF - C:\AdwCleaner[S2].txt - [1295 octets] ##########
_________________
 |
|
| Revenir en haut de page |
|
 |
zaede
Equipe de sécurité
Inscrit le: 07 Déc 2007
Messages: 593
Localisation: est
|
 Posté le: 05 Avr 2012 à 17:09 Sujet du message: Posté le: 05 Avr 2012 à 17:09 Sujet du message: |
 |
|
Bonjour joem
Il y avait une etape 3 à faire
Je la remet et un complément avec cette infection zeroaccess
Étape 1
Télécharge AntiZeroAcces
Lance le:
Répond Yes (oui) à la question, en tapant sur Y puis Entrée
Si le fix trouve l’infection, des lignes rouges doivent apparaître.
Le fix informe qu’un des fichiers systèmes a été patché et propose de le nettoyer.
Tape Y (oui) et Entrée pour lancer le nettoyage.
Si l’opération a réussi, tu verras le message Cleaned en vert.
Appuie sur une touche et redémarre l’ordinateur.
Étape 2
Télécharge FixZeroAccess
Un fix conçu par Norton. Enregistre ce fichier sur le bureau.
Quitte tous les programmes en cours, désactive tous les outils de sécurité (Antivirus, antispyware ect ...)
Clic droit sur FixZeroAccess.exe et Exécuter en tant qu'administrateur
Accepte la licence et clique sur Proceed
Laisse l'outil travailler ne touche ni au clavier ni à la souris
L'outil te demandera de redémarrer ton pc accepte
Après le redémarrage des informations sur l'infection seront affichées
Par mesure de sécurité refais un second scan avec FixZeroAccess |
|
| Revenir en haut de page |
|
 |
zaede
Equipe de sécurité
Inscrit le: 07 Déc 2007
Messages: 593
Localisation: est
|
 Posté le: 06 Avr 2012 à 21:57 Sujet du message: Posté le: 06 Avr 2012 à 21:57 Sujet du message: |
 |
|
Bonsoir joem
Poste un nouveau scan de roguekiller stp |
|
| Revenir en haut de page |
|
 |
joem
Modérateur

Inscrit le: 28 Jan 2006
Messages: 295
Localisation: a coté de trignac
|
 Posté le: 06 Avr 2012 à 22:56 Sujet du message: Posté le: 06 Avr 2012 à 22:56 Sujet du message: |
 |
|
Bonsoir Zaede,
Voici le rapport Roguekiller.
RogueKiller V7.3.2 [20/03/2012] par Tigzy
mail: tigzyRK<at>gmail<dot>com
Remontees: http://www.sur-la-toile.com/discussion-193725-1-BRogueKillerD-Remontees.html
Blog: http://tigzyrk.blogspot.com
Systeme d'exploitation: Windows XP (5.1.2600 Service Pack 3) 32 bits version
Demarrage : Mode normal
Utilisateur: Joem [Droits d'admin]
Mode: Recherche -- Date: 06/04/2012 22:52:27
¤¤¤ Processus malicieux: 0 ¤¤¤
¤¤¤ Entrees de registre: 0 ¤¤¤
¤¤¤ Fichiers / Dossiers particuliers: ¤¤¤
¤¤¤ Driver: [CHARGE] ¤¤¤
SSDT[25] : NtClose @ 0x80567AED -> HOOKED (Unknown @ 0xF8C8A7D4)
SSDT[41] : NtCreateKey @ 0x8057376F -> HOOKED (Unknown @ 0xF8C8A78E)
SSDT[50] : NtCreateSection @ 0x80565333 -> HOOKED (Unknown @ 0xF8C8A7DE)
SSDT[53] : NtCreateThread @ 0x80578803 -> HOOKED (Unknown @ 0xF8C8A784)
SSDT[63] : NtDeleteKey @ 0x80597FFA -> HOOKED (Unknown @ 0xF8C8A793)
SSDT[65] : NtDeleteValueKey @ 0x80595C1A -> HOOKED (Unknown @ 0xF8C8A79D)
SSDT[68] : NtDuplicateObject @ 0x805748C2 -> HOOKED (Unknown @ 0xF8C8A7CF)
SSDT[98] : NtLoadKey @ 0x805AF5C3 -> HOOKED (Unknown @ 0xF8C8A7A2)
SSDT[122] : NtOpenProcess @ 0x80574AA9 -> HOOKED (Unknown @ 0xF8C8A770)
SSDT[128] : NtOpenThread @ 0x8059323B -> HOOKED (Unknown @ 0xF8C8A775)
SSDT[177] : NtQueryValueKey @ 0x8056A419 -> HOOKED (Unknown @ 0xF8C8A7F7)
SSDT[193] : NtReplaceKey @ 0x8064FE82 -> HOOKED (Unknown @ 0xF8C8A7AC)
SSDT[200] : NtRequestWaitReplyPort @ 0x8056DC86 -> HOOKED (Unknown @ 0xF8C8A7E8)
SSDT[204] : NtRestoreKey @ 0x8064FA19 -> HOOKED (Unknown @ 0xF8C8A7A7)
SSDT[213] : NtSetContextThread @ 0x8062E33F -> HOOKED (Unknown @ 0xF8C8A7E3)
SSDT[237] : NtSetSecurityObject @ 0x8059D2BD -> HOOKED (Unknown @ 0xF8C8A7ED)
SSDT[247] : NtSetValueKey @ 0x8057BC5B -> HOOKED (Unknown @ 0xF8C8A798)
SSDT[255] : NtSystemDebugControl @ 0x8064AA57 -> HOOKED (Unknown @ 0xF8C8A7F2)
SSDT[257] : NtTerminateProcess @ 0x805839B9 -> HOOKED (Unknown @ 0xF8C8A77F)
S_SSDT[549] : Unknown -> HOOKED (Unknown @ 0xF8C8A806)
S_SSDT[552] : Unknown -> HOOKED (Unknown @ 0xF8C8A80B)
IRP[IRP_MJ_INTERNAL_DEVICE_CONTROL] : atapi.sys -> HOOKED ([MAJOR] prosync1.sys @ 0xF8A3F6C1)
¤¤¤ Infection : ZeroAccess ¤¤¤
[ZeroAccess] (LOCKED) windir\NtUpdateKBxxxx present!
¤¤¤ Fichier HOSTS: ¤¤¤
127.0.0.1 localhost
¤¤¤ MBR Verif: ¤¤¤
+++++ PhysicalDrive0: WDC WD1600AAJB-22WRA0 +++++
--- User ---
[MBR] 9b8fe57175eadd014c86f40063d33463
[BSP] 70dd8b4b891dfafb3a751a70cfbce75c : Windows XP MBR Code
Partition table:
0 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 63 | Size: 49999 Mo
1 - [XXXXXX] EXTEN-LBA (0x0f) [VISIBLE] Offset (sectors): 102398310 | Size: 102618 Mo
User = LL1 ... OK!
User = LL2 ... OK!
Termine : << RKreport[4].txt >>
RKreport[1].txt ; RKreport[2].txt ; RKreport[3].txt ; RKreport[4].txt
_________________
 |
|
| Revenir en haut de page |
|
 |
zaede
Equipe de sécurité
Inscrit le: 07 Déc 2007
Messages: 593
Localisation: est
|
 Posté le: 07 Avr 2012 à 11:45 Sujet du message: Posté le: 07 Avr 2012 à 11:45 Sujet du message: |
 |
|
Bonjour joem, on va passer à autre chose
1. Télécharge combofix.exe (par sUBs) sur le bureau à l'aide d'un des liens ci-dessous:
http://download.bleepingcomputer.com/sUBs/ComboFix.exe
http://subs.geekstogo.com/ComboFix.exe
Installe la console de récupération si cela est demandé en suivant soigneusement les instructions qui s'afficheront
Ferme le navigateur et tous les programmes ouverts
Désactive tous les logiciels de sécurité (antivirus antimalwares spybot etc) et ne clique pas dans la fenêtre pendant l'exécution du scan
2. Fais un double clic sur ComboFix.exe, laisse ensuite le scan se dérouler sans toucher à la souris ni au clavier.
3. Lorsque le scan sera complété, un rapport apparaitra. Copie/colle ce rapport dans ta prochaine réponse.
Le rapport se trouve également ici : C:\Combofix.txt
NOTE:
Combofix peut être détecté par certains antivirus.
Ne pas en tenir compte, c'est un faux positif
Cliquer sur ignorer et continuer la procédure
Lié au module AS (Additional Scan). Il permet de lister certaines clés de registre ou certains dossiers. Il s'agit proncipalement de cibler les : |
|
| Revenir en haut de page |
|
 |
joem
Modérateur

Inscrit le: 28 Jan 2006
Messages: 295
Localisation: a coté de trignac
|
 Posté le: 24 Avr 2012 à 19:39 Sujet du message: Posté le: 24 Avr 2012 à 19:39 Sujet du message: |
 |
|
Bonsoir zaede,
Voici le rapport du scan avec un peu de retard 
ComboFix 12-04-24.02 - Joem 24/04/2012 19:05:10.1.1 - x86
Lancé depuis: e:\documents\TÚlÚchargements\ComboFix.exe
AV: Avira Desktop *Disabled/Updated* {AD166499-45F9-482A-A743-FDD3350758C7}
.
.
(((((((((((((((((((((((((((((((((((( Autres suppressions ))))))))))))))))))))))))))))))))))))))))))))))))
.
.
C:\userinit.exe
c:\windows\$NtUninstallKB48791$
c:\windows\$NtUninstallKB48791$\1569383197\@
c:\windows\$NtUninstallKB48791$\1569383197\L(2)\chuffaef
c:\windows\$NtUninstallKB48791$\788748783
.
.
((((((((((((((((((((((((((((((((((((((( Pilotes/Services )))))))))))))))))))))))))))))))))))))))))))))))))
.
.
-------\Legacy_6TO4
-------\Service_6to4
.
.
((((((((((((((((((((((((((((( Fichiers créés du 2012-03-24 au 2012-04-24 ))))))))))))))))))))))))))))))))))))
.
.
2012-04-15 08:57 . 2008-04-13 11:19 75264 ----a-w- c:\windows\system32\drivers\ipsec.sys
2012-04-11 18:41 . 2002-11-21 15:35 49264 ----a-r- c:\windows\system32\drivers\fhlpppoe.sys
2012-04-11 18:41 . 2002-04-02 15:04 147456 ----a-r- c:\windows\system32\pppoe32.dll
2012-04-11 18:41 . 2005-06-22 14:21 118784 ----a-r- c:\windows\bwnsetup.exe
2012-04-11 18:41 . 2012-04-11 18:41 -------- d-----w- c:\program files\BeWAN ADSL2+ Combo
2012-04-10 12:51 . 2012-04-10 12:51 -------- d-----w- c:\documents and settings\Joem\Local Settings\Application Data\Help
2012-04-09 17:31 . 2003-01-16 04:17 40960 ----a-r- c:\windows\system32\drivers\fetnd5b.sys
2012-04-09 17:31 . 2002-09-13 00:29 6016 ----a-r- c:\windows\system32\ntsim.sys
2012-04-09 17:28 . 2001-08-17 18:13 27165 -c--a-w- c:\windows\system32\dllcache\fetnd5.sys
2012-04-09 17:28 . 2001-08-17 18:13 27165 ----a-w- c:\windows\system32\drivers\fetnd5.sys
2012-04-09 17:16 . 2003-04-15 08:59 5824 ----a-w- c:\windows\system32\drivers\ASUSHWIO.SYS
2012-04-07 21:40 . 2012-04-07 21:40 -------- d-----w- c:\windows\system32\wbem\Repository
2012-04-07 21:22 . 2012-04-07 21:22 -------- d-----w- C:\found.000
2012-04-07 17:28 . 2011-08-17 13:49 138496 ----a-w- c:\windows\system32\drivers\afd.sys
2012-04-05 19:51 . 2012-04-05 19:51 -------- d-----w- c:\documents and settings\Joem\Application Data\FixZeroAccess
2012-04-02 21:05 . 2012-04-03 20:03 -------- d-----w- C:\ZHP
2012-04-02 21:04 . 2012-04-02 22:22 -------- d-----w- c:\program files\ZHPDiag
2012-03-31 21:37 . 2012-03-31 21:37 -------- d-sh--w- c:\documents and settings\NetworkService\PrivacIE
2012-03-31 21:35 . 2012-03-31 21:35 -------- d-sh--w- c:\documents and settings\NetworkService\IETldCache
2012-03-31 21:35 . 2012-03-31 21:37 -------- d-----r- c:\documents and settings\NetworkService\Favoris
2012-03-31 07:27 . 2012-04-15 10:05 418464 ----a-w- c:\windows\system32\FlashPlayerApp.exe
2012-03-26 15:41 . 2012-03-26 15:41 103864 ----a-w- c:\program files\Mozilla Firefox\plugins\nppdf32.dll
2012-03-26 15:41 . 2012-03-26 15:41 103864 ----a-w- c:\program files\Internet Explorer\PLUGINS\nppdf32.dll
2012-03-26 14:50 . 2012-04-07 06:59 -------- d-----w- c:\windows\system32\NtmsData
.
.
.
(((((((((((((((((((((((((((((((((( Compte-rendu de Find3M ))))))))))))))))))))))))))))))))))))))))))))))))
.
2012-04-15 10:05 . 2011-06-03 05:55 70304 ----a-w- c:\windows\system32\FlashPlayerCPLApp.cpl
2012-03-01 11:00 . 2004-08-19 14:09 916992 ----a-w- c:\windows\system32\wininet.dll
2012-03-01 11:00 . 2004-08-19 14:10 1469440 ------w- c:\windows\system32\inetcpl.cpl
2012-03-01 11:00 . 2004-08-19 14:09 43520 ----a-w- c:\windows\system32\licmgr10.dll
2012-02-29 14:10 . 2004-08-19 14:09 177664 ----a-w- c:\windows\system32\wintrust.dll
2012-02-29 14:10 . 2004-08-19 14:09 148480 ----a-w- c:\windows\system32\imagehlp.dll
2012-02-29 12:17 . 2004-08-19 13:56 385024 ----a-w- c:\windows\system32\html.iec
2012-02-03 09:58 . 2004-08-19 14:00 1860224 ----a-w- c:\windows\system32\win32k.sys
2012-01-31 07:57 . 2012-03-03 16:46 137416 ----a-w- c:\windows\system32\drivers\avipbb.sys
2012-01-31 07:57 . 2009-12-12 11:48 74640 ----a-w- c:\windows\system32\drivers\avgntflt.sys
2012-03-18 22:43 . 2011-12-02 07:05 97208 ----a-w- c:\program files\mozilla firefox\components\browsercomps.dll
.
.
((((((((((((((((((((((((((((((((( Points de chargement Reg ))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* les éléments vides & les éléments initiaux légitimes ne sont pas listés
REGEDIT4
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\DropboxExt1]
@="{FB314ED9-A251-47B7-93E1-CDD82E34AF8B}"
[HKEY_CLASSES_ROOT\CLSID\{FB314ED9-A251-47B7-93E1-CDD82E34AF8B}]
2011-12-05 19:17 94208 ----a-w- c:\documents and settings\Joem\Application Data\Dropbox\bin\DropboxExt.14.dll
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\DropboxExt2]
@="{FB314EDA-A251-47B7-93E1-CDD82E34AF8B}"
[HKEY_CLASSES_ROOT\CLSID\{FB314EDA-A251-47B7-93E1-CDD82E34AF8B}]
2011-12-05 19:17 94208 ----a-w- c:\documents and settings\Joem\Application Data\Dropbox\bin\DropboxExt.14.dll
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\DropboxExt3]
@="{FB314EDB-A251-47B7-93E1-CDD82E34AF8B}"
[HKEY_CLASSES_ROOT\CLSID\{FB314EDB-A251-47B7-93E1-CDD82E34AF8B}]
2011-12-05 19:17 94208 ----a-w- c:\documents and settings\Joem\Application Data\Dropbox\bin\DropboxExt.14.dll
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\DropboxExt4]
@="{FB314EDC-A251-47B7-93E1-CDD82E34AF8B}"
[HKEY_CLASSES_ROOT\CLSID\{FB314EDC-A251-47B7-93E1-CDD82E34AF8B}]
2011-12-05 19:17 94208 ----a-w- c:\documents and settings\Joem\Application Data\Dropbox\bin\DropboxExt.14.dll
.
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"TomTomHOME.exe"="c:\program files\TomTom HOME 2\TomTomHOMERunner.exe" [2012-01-23 247728]
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"QuickTime Task"="c:\program files\QuickTime\qttask.exe" [2009-11-10 417792]
"SunJavaUpdateSched"="c:\program files\Fichiers communs\Java\Java Update\jusched.exe" [2011-06-09 254696]
"adm_tray.exe"="c:\program files\Acronis\DriveMonitor\adm_tray.exe" [2011-02-24 470240]
"Service Planificateur2 Acronis"="c:\program files\Fichiers communs\Acronis\Schedule2\schedhlp.exe" [2011-02-12 365632]
"Adobe Reader Speed Launcher"="c:\program files\Adobe\Reader 9.0\Reader\Reader_sl.exe" [2012-03-27 37296]
"Adobe ARM"="c:\program files\Fichiers communs\Adobe\ARM\1.0\AdobeARM.exe" [2012-01-02 843712]
"avgnt"="c:\program files\Avira\AntiVir Desktop\avgnt.exe" [2012-01-31 258512]
.
[HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Run]
"CTFMON.EXE"="c:\windows\system32\CTFMON.EXE" [2008-04-13 15360]
.
c:\documents and settings\Joem\Menu Démarrer\Programmes\Démarrage\
Dropbox.lnk - c:\documents and settings\Joem\Application Data\Dropbox\bin\Dropbox.exe [2012-2-15 24246216]
ZooskMessenger.lnk - c:\program files\ZooskMessenger\ZooskMessenger.exe [N/A]
.
c:\documents and settings\All Users\Menu Démarrer\Programmes\Démarrage\
HP Digital Imaging Monitor.lnk - c:\program files\HP\Digital Imaging\bin\hpqtra08.exe [2006-2-19 288472]
PHOTOfunSTUDIO 5.0.lnk - c:\program files\Fichiers communs\Panasonic\PHOTOfunSTUDIO AutoStart\AutoStartupService.exe [2011-7-5 172544]
.
[HKEY_USERS\.default\software\microsoft\windows\currentversion\policies\system]
"DisableRegedit"= 1 (0x1)
.
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Smapp]
2003-05-05 07:57 143360 ----a-w- c:\program files\Analog Devices\SoundMAX\SMTray.exe
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile]
"EnableFirewall"= 0 (0x0)
.
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqtra08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqste08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpofxm08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hposfx08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hposid01.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqscnvw.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqkygrp.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqCopy.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpfccopy.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpzwiz01.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\Unload\\HpqPhUnl.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\Unload\\HpqDIA.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpoews01.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqnrs08.exe"=
"c:\\Program Files\\uTorrent\\uTorrent.exe"=
"c:\\Program Files\\Java\\jre6\\bin\\java.exe"=
"c:\\Program Files\\Windows Live\\Messenger\\wlcsdk.exe"=
"c:\\Program Files\\Windows Live\\Messenger\\msnmsgr.exe"=
"c:\\Documents and Settings\\Joem\\Application Data\\Dropbox\\bin\\Dropbox.exe"=
"c:\\Program Files\\Mozilla Firefox\\firefox.exe"=
.
R1 avkmgr;avkmgr;c:\windows\system32\drivers\avkmgr.sys [03/03/2012 18:46 36000]
R2 AntiVirSchedulerService;Avira Scheduler;c:\program files\Avira\AntiVir Desktop\sched.exe [03/03/2012 18:46 86224]
R2 TomTomHOMEService;TomTomHOMEService;c:\program files\TomTom HOME 2\TomTomHOMEService.exe [23/01/2012 06:43 92592]
R3 fhlppppoe;PPPOE/ADSL miniport;c:\windows\system32\drivers\fhlpppoe.sys [11/04/2012 20:41 49264]
S3 AdobeFlashPlayerUpdateSvc;Adobe Flash Player Update Service;c:\windows\system32\Macromed\Flash\FlashPlayerUpdateService.exe [31/03/2012 09:27 253088]
S3 cpuz135;cpuz135;\??\c:\docume~1\Joem\LOCALS~1\Temp\cpuz135\cpuz135_x32.sys --> c:\docume~1\Joem\LOCALS~1\Temp\cpuz135\cpuz135_x32.sys [?]
.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost - NetSvcs
imap4d32
klblmain
symantecantibotshim
emitray
softfax
CTSBLFX.DLL
AF15BDA
Defrag32b
omniinet
syslogd
MASPINT
mssqlserveradhelper
tfsncofs
rasirda
SNTIE
Stltrk2k
radclock
mcusrmgr
winsshd
dsunidrv
spupdsvc
uhcd
tosrfbnp
InCDsrvR
oracle_load_balancer_60_server-forms6i
pclepci
.
Contenu du dossier 'Tâches planifiées'
.
2012-04-24 c:\windows\Tasks\Adobe Flash Player Updater.job
- c:\windows\system32\Macromed\Flash\FlashPlayerUpdateService.exe [2012-03-31 10:05]
.
2011-07-05 c:\windows\Tasks\AppleSoftwareUpdate.job
- c:\program files\Apple Software Update\SoftwareUpdate.exe [2008-07-30 10:34]
.
2012-04-22 c:\windows\Tasks\Google Software Updater.job
- c:\program files\Google\Common\Google Updater\GoogleUpdaterService.exe [2009-01-19 07:55]
.
2012-04-24 c:\windows\Tasks\User_Feed_Synchronization-{17FE69FE-C828-4BE2-97B4-8391E6123245}.job
- c:\windows\system32\msfeedssync.exe [2009-03-08 02:31]
.
2012-04-24 c:\windows\Tasks\WGASetup.job
- c:\windows\system32\KB905474\wgasetup.exe [2009-08-24 20:18]
.
.
------- Examen supplémentaire -------
.
DPF: Microsoft XML Parser for Java - file:///C:/WINDOWS/Java/classes/xmldso.cab
FF - ProfilePath - c:\documents and settings\Joem\Application Data\Mozilla\Firefox\Profiles\fmwyab9z.default\
FF - prefs.js: browser.startup.homepage - hxxp://www.google.fr
FF - prefs.js: keyword.URL - hxxp://www.google.com/search?ie=UTF-8&oe=UTF-8&sourceid=navclient&gfns=1&q=
.
.
**************************************************************************
.
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2012-04-24 19:18
Windows 5.1.2600 Service Pack 3 NTFS
.
Recherche de processus cachés ...
.
Recherche d'éléments en démarrage automatique cachés ...
.
Recherche de fichiers cachés ...
.
Scan terminé avec succès
Fichiers cachés: 0
.
**************************************************************************
.
--------------------- CLES DE REGISTRE BLOQUEES ---------------------
.
[HKEY_USERS\.Default\Software\Microsoft\Internet Explorer\User Preferences]
@Denied: (2) (LocalSystem)
"88D7D0879DAB32E14DE5B3A805A34F98AFF34F5977"=hex:01,00,00,00,d0,8c,9d,df,01,15,
d1,11,8c,7a,00,c0,4f,c2,97,eb,01,00,00,00,b4,7c,0d,78,90,45,d7,48,a0,ff,97,\
"2D53CFFC5C1A3DD2E97B7979AC2A92BD59BC839E81"=hex:01,00,00,00,d0,8c,9d,df,01,15,
d1,11,8c,7a,00,c0,4f,c2,97,eb,01,00,00,00,b4,7c,0d,78,90,45,d7,48,a0,ff,97,\
.
[HKEY_USERS\S-1-5-21-73586283-527237240-725345543-1003\Software\Microsoft\SystemCertificates\AddressBook*]
@Allowed: (Read) (RestrictedCode)
@Allowed: (Read) (RestrictedCode)
.
--------------------- DLLs chargées dans les processus actifs ---------------------
.
- - - - - - - > 'explorer.exe'(2320)
c:\documents and settings\Joem\Application Data\Dropbox\bin\DropboxExt.14.dll
c:\windows\system32\webcheck.dll
c:\windows\system32\eappprxy.dll
.
------------------------ Autres processus actifs ------------------------
.
c:\program files\Fichiers communs\Acronis\Schedule2\schedul2.exe
c:\program files\Avira\AntiVir Desktop\avguard.exe
c:\program files\Java\jre6\bin\jqs.exe
c:\program files\CDBurnerXP\NMSAccessU.exe
c:\program files\Microsoft\Search Enhancement Pack\SeaPort\SeaPort.exe
c:\program files\Analog Devices\SoundMAX\SMAgent.exe
c:\program files\HP\Digital Imaging\bin\hpqSTE08.exe
c:\program files\Avira\AntiVir Desktop\avshadow.exe
c:\windows\system32\wscntfy.exe
.
**************************************************************************
.
Heure de fin: 2012-04-24 19:23:38 - La machine a redémarré
ComboFix-quarantined-files.txt 2012-04-24 17:23
ComboFix2.txt 2012-04-07 17:55
.
Avant-CF: 32 406 859 776 octets libres
Après-CF: 32 419 061 760 octets libres
.
- - End Of File - - B794BDED146E634CE3DFCE9362C2F0D7
_________________
 |
|
| Revenir en haut de page |
|
 |
zaede
Equipe de sécurité
Inscrit le: 07 Déc 2007
Messages: 593
Localisation: est
|
 Posté le: 25 Avr 2012 à 15:12 Sujet du message: Posté le: 25 Avr 2012 à 15:12 Sujet du message: |
 |
|
Bonjour joem
C'est mieux apres combofix? |
|
| Revenir en haut de page |
|
 |
joem
Modérateur

Inscrit le: 28 Jan 2006
Messages: 295
Localisation: a coté de trignac
|
 Posté le: 25 Avr 2012 à 19:12 Sujet du message: Posté le: 25 Avr 2012 à 19:12 Sujet du message: |
 |
|
Bonsoir zaede,
Oui beaucoup mieux, seulement l'antivirus m'a détecté une seule fois aujourd'hui "tr/crypt.XPACK.Gen8"
_________________
 |
|
| Revenir en haut de page |
|
 |
zaede
Equipe de sécurité
Inscrit le: 07 Déc 2007
Messages: 593
Localisation: est
|
 Posté le: 27 Avr 2012 à 22:40 Sujet du message: Posté le: 27 Avr 2012 à 22:40 Sujet du message: |
 |
|
Bonjour joem
Tu as le chemin complet de ce fichier detecté? |
|
| Revenir en haut de page |
|
 |
joem
Modérateur

Inscrit le: 28 Jan 2006
Messages: 295
Localisation: a coté de trignac
|
 Posté le: 28 Avr 2012 à 0:15 Sujet du message: Posté le: 28 Avr 2012 à 0:15 Sujet du message: |
 |
|
Bonsoir zaede,
The file 'C:\System Volume Information\_restore{BA127E5C-6276-4D76-8184-B96B8A406D7E}\RP1069\A0063002.exe'
contained a virus or unwanted program 'TR/Drop.Injector.dzml' [trojan]
Action(s) taken:
The file was moved to the quarantine directory under the name '4c81b0a9.qua'.
_________________
 |
|
| Revenir en haut de page |
|
 |
zaede
Equipe de sécurité
Inscrit le: 07 Déc 2007
Messages: 593
Localisation: est
|
 Posté le: 28 Avr 2012 à 23:06 Sujet du message: Posté le: 28 Avr 2012 à 23:06 Sujet du message: |
 |
|
Bonjour joem
C'est un fichier situé dans les points de restauration
- Désactive la restauration du système sur tous les lecteurs :
Tuto ou ici
- Redémarre <== très important
- Refait un scan antivirus et poste le rapport si possible
- Réactive la restauration du système (important) |
|
| Revenir en haut de page |
|
 |
Ajouter à : 



|
|
 Ce que nous vous conseillons :
Ce que nous vous conseillons :
















 (coller les lignes helper)
(coller les lignes helper)


